Encryption is an effective method of protecting digital data. Information is converted or encoded into a code called cipher text, which cannot be understood by anyone except authorized parties. To read an encrypted file, you must have access to the encryption password that enables you to decrypt it.
If your files contain sensitive information, you can use passwords to restrict certain people from opening your documents, workbooks or presentations in Microsoft Office. Keep in mind that encrypted documents cannot be opened, if these passwords are lost or forgotten! We recommend using our printable template to log passwords. Please store your list in a safe place!
If your files contain sensitive information, you can use passwords to restrict certain people from opening your documents, workbooks or presentations in Microsoft Office. Keep in mind that encrypted documents cannot be opened, if these passwords are lost or forgotten! We recommend using our printable template to log passwords. Please store your list in a safe place!
How To Password Protect Opening Workbooks in Excel
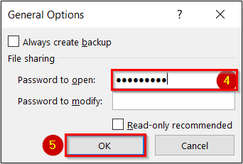
Open a workbook, navigate to the Save As dialog box (File > Save As > Browse), then click the Tools drop-down menu near the bottom of the dialog box. Open the Tools menu & select General Options
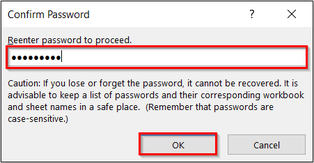
Type in your desired password in the password-to-open field. Click OK. You will be asked to verify your password by entering it in again. Now, your file has an encryption password to prevent unauthorized people from opening up and viewing your Excel workbook.
Finally, click the Save button to convert your file in an encrypted format using the AES algorithm.
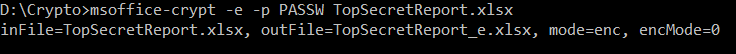
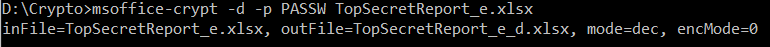
Encrypt or Decrypt Office Files With A Command Line Utility!
|
Shigeo Mitsunari is an ingenious world class security expert and Microsoft MVP, who developed a free command line tool to encrypt and decrypt OpenXML Office files. The VC++ utility is licensed under a permissive BSD license and is available for download at his GitHub project page (@herumi) under the bin folder.
|
The tool was developed as a proof of concept to demonstrate that backdooring Microsoft Office documents with secret master keys is feasible. You can read about his presentation at the Code Blue 2015 international security conference in Japan here.
In summary, Shigeo along with his friend and Microsoft MVP Yoshinori Takesako discovered a vulnerability in the file format specification that may allow an attacker to decrypt strongly encrypted Office documents without knowing the passwords! This is possible by tricking MS Office into creating an undetectable secret master key, when encrypted documents are created. Then, an attacker can use the master key to decrypt almost instantly Office documents, no matter what file open password was used.
I read the presentation and I encourage every IT admin or developer who is security minded to do so. The attack does not seem easy to deploy on desktop installtions undetected. However, the authors claim that it would be much easier to backdoor encryption in an undetectable manner in cloud environments.
In summary, Shigeo along with his friend and Microsoft MVP Yoshinori Takesako discovered a vulnerability in the file format specification that may allow an attacker to decrypt strongly encrypted Office documents without knowing the passwords! This is possible by tricking MS Office into creating an undetectable secret master key, when encrypted documents are created. Then, an attacker can use the master key to decrypt almost instantly Office documents, no matter what file open password was used.
I read the presentation and I encourage every IT admin or developer who is security minded to do so. The attack does not seem easy to deploy on desktop installtions undetected. However, the authors claim that it would be much easier to backdoor encryption in an undetectable manner in cloud environments.
How The Command Line Tool Works
Hacking aside, normal Office users or developers can use this utility to encrypt or decrypt closed files from the command line in a batch process. Files are encrypted with the same strong AES algorithm (128 or 256) as used by Office. Password opening protection can be removed almost instantly from files in batch, if passwords are known. The tool was tested with both Transitional and Strict ISO 29500 OOXML Excel files.
Your files cannot be recovered, if passwords are lost, unless your Office installation is' backdoored'. Please don't contact me to send you how-to instructions, as I honestly do not know how it is done!
There is an important difference between using this utility and encrypting files using Office 2013 (or later). When using Excel, Word and PowerPoint a public key information can be saved in the file header. The administrator can use this public key and matching private key later, if asked, to remove the password protection. Microsoft allows IT admins to configure the Escrow key feature options to gain access to password protected files, if passwords are lost or forgotten. Read about Microsoft's free DocRecrypt tool here and download it here.
Your files cannot be recovered, if passwords are lost, unless your Office installation is' backdoored'. Please don't contact me to send you how-to instructions, as I honestly do not know how it is done!
There is an important difference between using this utility and encrypting files using Office 2013 (or later). When using Excel, Word and PowerPoint a public key information can be saved in the file header. The administrator can use this public key and matching private key later, if asked, to remove the password protection. Microsoft allows IT admins to configure the Escrow key feature options to gain access to password protected files, if passwords are lost or forgotten. Read about Microsoft's free DocRecrypt tool here and download it here.
However, your top secret files encrypted with Shigeo's utility cannot be decrypted with Microsoft's DocRecrypt tool under any circumstances.
Copy msoffice-crypt.exe, the executable 32-bit binary file, from the Github (bin folder) to your PC. Installation is not required, as the file is portable. Ideally, compile the source code in your machine, if you can do so. Visual C++ Redistributable for Visual Studio may be required on the target Windows computer, if the project is compiled without the /MT option.
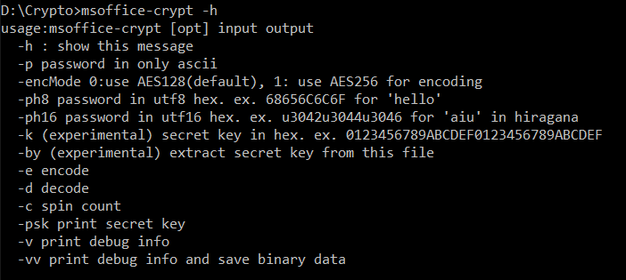
Command Line Syntax
How To Know If Your Office Has Been Hacked!
|
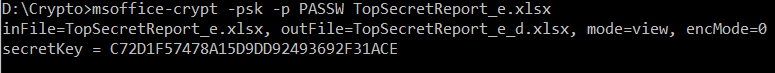
Each secret key should be distinct (unique) in every encrypted file. Secret keys can be used to encrypt or decrypt a file when used with the -k switch, instead of using a password. Only if your Office installation has been hacked (backdoored), the secret key will be identical in every encrypted file.
|
Here are the detailed steps recommended by Shigeo to verify that security of your Office 2010 or later software has not be compromised:
- Verify that the source code of the utility published in GitHub does not contain any malicious code.
- Create your own executable by compiling the verified source code on a clean computer
- Sign the executable with your digital certificate
- Create a secret key using a one-time pad key generator
- Compile tool on a Windows computer. Use it to encypt a file on Windows with the the -k option and the above secret key
- Compile tool on a Linux computer. Use it on Linux to verify that the encrypted file has the same secret key using the -psk option
A quick-and-dirty approach to verify integrity of your Office installation is to encrypt at least 2 files with a unique password using Excel, PowerPoint or Word. Then, print and compare the secret keys for each file shown by the -psk option. Secret keys must be unique! Watch a demo video in YouTube!
Please note that secret keys are not available for OOXML files encrypted in Office 2007. Only Office 2010 or later supports advanced Agile encryption.
Please note that secret keys are not available for OOXML files encrypted in Office 2007. Only Office 2010 or later supports advanced Agile encryption.
About The Software Author
Shigeo Mitsunari is a researcher and developer of security and infrastructure at Cybozu Labs, Inc, Japan. He developed and published the world's fastest library implementation for pairing-based cryptography on GitHub. In 2010, he won IEICE Best Paper Award for his research on the vector decomposition problem. In 2015, he won the Microsoft MVP Developer award in the field of security. He is the author of 'Applied Cryptography for the Cloud'.